This web page was created programmatically, to learn the article in its unique location you possibly can go to the hyperlink bellow:
https://arstechnica.com/gadgets/2025/10/leaker-reveals-which-pixels-are-vulnerable-to-cellebrite-phone-hacking/
and if you wish to take away this text from our website please contact us
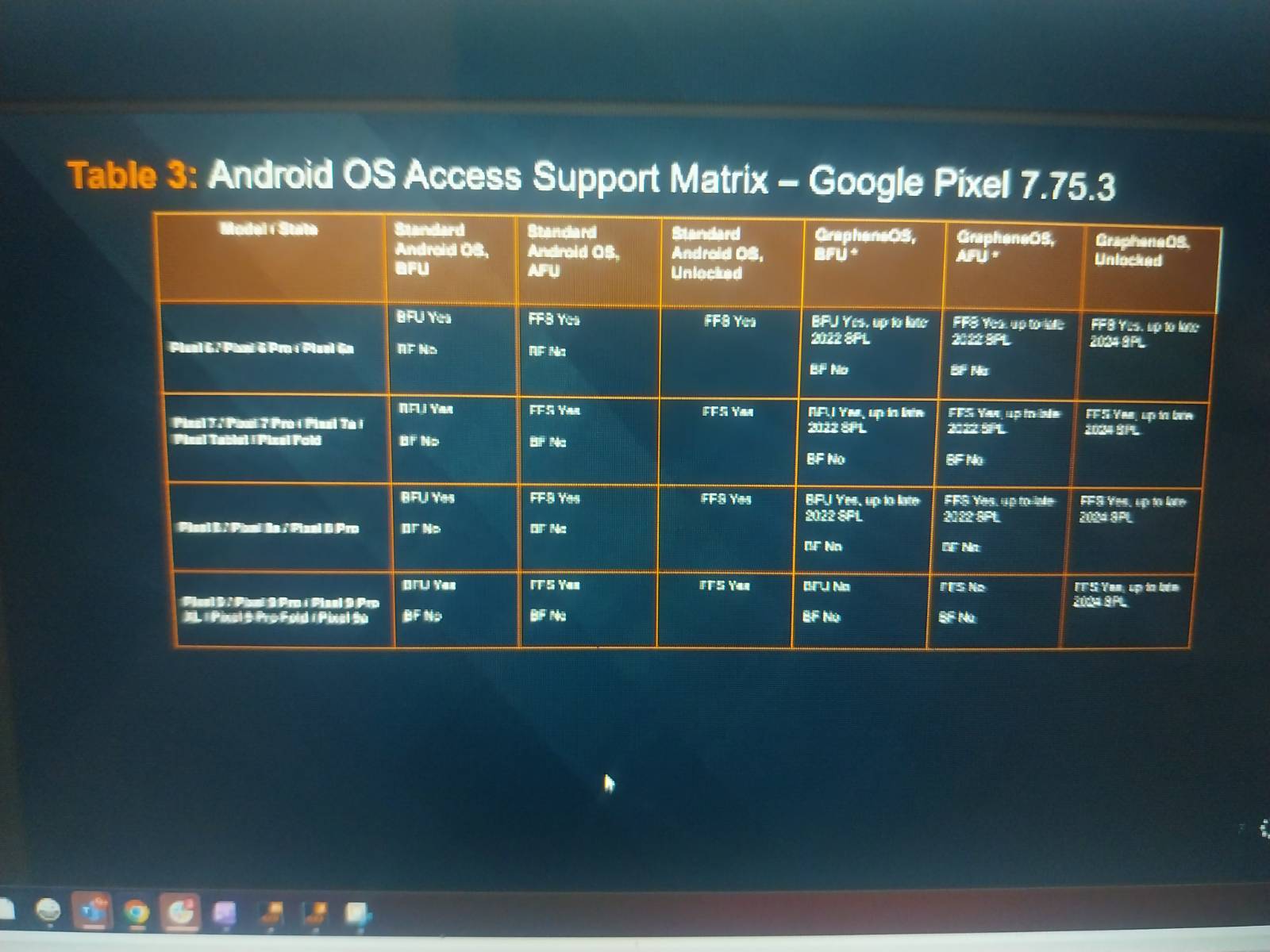
This blurry screenshot seems to checklist which Pixel telephones Cellebrite units can hack.
Credit:
rogueFed
At least in keeping with Cellebrite, GrapheneOS is safer than what Google gives out of the field. The firm is telling legislation enforcement in these briefings that its know-how can extract knowledge from Pixel 6, 7, 8, and 9 telephones in unlocked, AFU, and BFU states on inventory software program. However, it can’t brute-force passcodes to allow full management of a tool. The leaker additionally notes legislation enforcement continues to be unable to repeat an eSIM from Pixel units. Notably, the Pixel 10 sequence is shifting away from bodily SIM playing cards.
For those self same telephones working GrapheneOS, police can anticipate to have a a lot tougher time. The Cellebrite desk says that Pixels with GrapheneOS are solely accessible when working software program from earlier than late 2022—each the Pixel 8 and Pixel 9 have been launched after that. Phones in each BFU and AFU states are protected from Cellebrite on up to date builds, and as of late 2024, even a totally unlocked GrapheneOS gadget is immune from having its knowledge copied. An unlocked cellphone might be inspected in loads of different methods, however knowledge extraction on this case is proscribed to what the consumer can entry.
The unique leaker claims to have dialed into two calls to this point with out detection. However, rogueFed additionally referred to as out the assembly organizer by identify (the second screenshot, which we’re not reposting). Odds are that Cellebrite can be screening assembly attendees extra rigorously now.
We’ve reached out to Google to inquire about why a customized ROM created by a small non-profit is extra proof against industrial cellphone hacking than the official Pixel OS. We’ll replace this text if Google has something to say.
This web page was created programmatically, to learn the article in its unique location you possibly can go to the hyperlink bellow:
https://arstechnica.com/gadgets/2025/10/leaker-reveals-which-pixels-are-vulnerable-to-cellebrite-phone-hacking/
and if you wish to take away this text from our website please contact us