This web page was created programmatically, to learn the article in its authentic location you may go to the hyperlink bellow:
https://cyberpress.org/researchers-use-call-gadgets/
and if you wish to take away this text from our web site please contact us
Security researchers have uncovered a complicated approach that exploits name devices to bypass Elastic EDR’s signature-based detection mechanisms.
The technique works by inserting arbitrary modules into the decision stack throughout module loading, successfully breaking the detection patterns that Elastic’s EDR engine depends upon to establish malicious exercise.
This improvement underscores the continued cat-and-mouse sport between risk actors and endpoint detection platforms.
The breakthrough leverages Elastic’s dedication to transparency, a double-edged sword within the safety panorama.
Unlike many enterprise safety distributors that hold their detection logic proprietary, Elastic publicly shares its detection guidelines and payload testing instruments.
This openness permits the safety neighborhood to totally perceive and problem EDR mechanisms, fostering innovation and collaboration.
However, it additionally gives attackers with a transparent roadmap to establish and circumvent detection methods.
How Elastic’s Detection Framework Works
Elastic EDR’s detection engine prioritizes name stack evaluation to establish suspicious exercise. The system carefully displays module masses initiated from unbacked reminiscence areas, code that exists solely in RAM moderately than on disk.
This habits is a trademark of malicious strategies like shellcode injection and in-memory code execution generally employed by command-and-control implants.
Specific detection guidelines seek for community modules loaded from unbacked reminiscence, flagging patterns that deviate from authentic utility habits.
Previous evasion makes an attempt used strategies equivalent to name stack spoofing and API proxying, which Elastic countered by introducing further detection guidelines focusing on these ways.
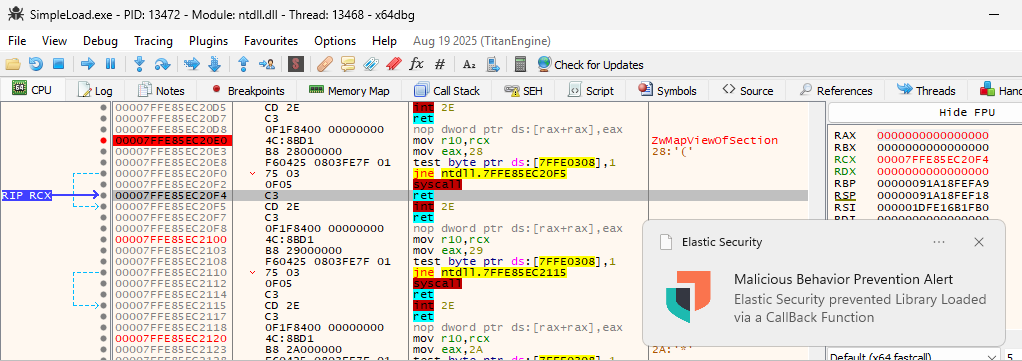
syscall instruction, the alert will set off:The vendor refined its strategy by specializing in particular system libraries to cut back false positives whereas sustaining detection efficacy.
The newly disclosed analysis introduces a novel technique: exploiting controllable name directions generally known as devices discovered inside system DLLs that aren’t at present focused by EDR signatures.
By manipulating these devices throughout community library loading operations, researchers insert an arbitrary module into the noticed name stack, disrupting the signature patterns that set off Elastic’s alerts.
The proof-of-concept demonstration utilized a particular call-return gadget from an older model of dsdmo.dll.
When this gadget is invoked throughout community library loading, equivalent to with wininet.dll, the inserted module seems within the name stack, breaking the anticipated detection signature.
The consequence: beforehand detectable operations now go unnoticed by the EDR agent.
This strategy builds upon established analysis into shellcode obfuscation and callback-based API proxying, however demonstrates a sensible methodology for locating actual devices in extensively accessible system DLLs.
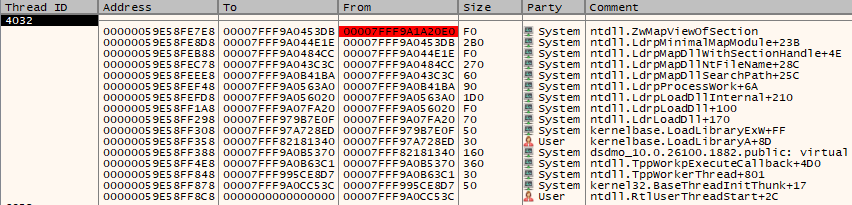
Although the examined gadget originates from a deprecated library model, the analysis gives a reproducible course of for figuring out comparable devices in present DLL units.
The researchers responsibly disclosed this evasion approach to Elastic, which is actively creating up to date detection guidelines to deal with this bypass vector.
This discovering highlights the vital significance of ongoing collaboration and transparency inside the cybersecurity neighborhood.
While this particular approach targets one detection mechanism, Elastic EDR maintains quite a few further detection alternatives all through an assault’s lifecycle, making it removed from out of date.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today
This web page was created programmatically, to learn the article in its authentic location you may go to the hyperlink bellow:
https://cyberpress.org/researchers-use-call-gadgets/
and if you wish to take away this text from our web site please contact us



